Risk Flagger Workflow
The Risk Flagger workflow analyzes code changes for security risks that require security team investigation. Unlike traditional vulnerability scanners, this workflow focuses on identifying changes that could introduce security risks, making it ideal for pull request analysis and change management.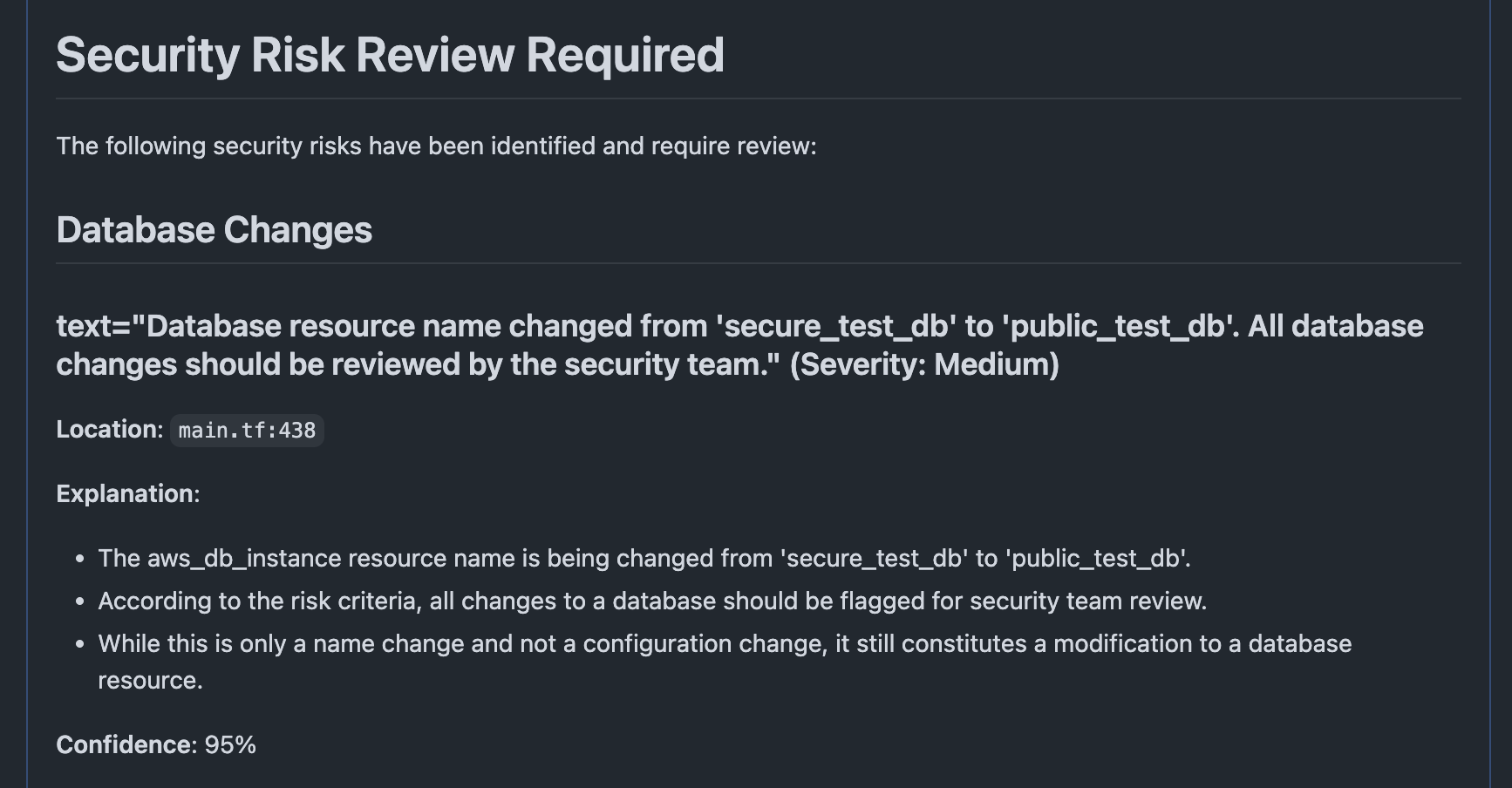
Overview
- Workflow ID:
risk_flagger - Primary Use Case: Risk assessment of code changes and pull requests
- Output: Risk findings and optional GitHub notifications
- Required Mode: Must use
--diffmode
Common Use Cases
1. Pull Request Security Gate
- CLI
- GitHub Actions
2. Custom Risk Categories
- CLI
- GitHub Actions
3. Release Branch Analysis
- CLI
- GitHub Actions
4. Pre-Commit Risk Assessment
- CLI
Workflow-Specific Options
Required Options
--diff
Required: The risk flagger workflow must run in diff mode.
GitHub Integration Options
--pr-url <URL>
URL of the pull request to analyze for GitHub integration.
--approver <USERNAME>
GitHub username or team to notify when risks are found.
--no-gh-comment <BOOLEAN>
Set to true to disable GitHub comments for risk findings. Useful when you want to use only Slack notifications or other notification methods.
Default: false
--should-block-pull-request <BOOLEAN> (GitHub Action only)
Whether to block the pull request until security review is complete. Available only when using the GitHub Action.
Default: false
--slack-webhook-url <URL>
Provide a Slack webhook URL to send risk notifications to your team’s Slack channel.
Customization Options
--custom-risk-list-action <append|replace>
How to handle custom risk lists.
Default: append
--custom-risk-list-filepath <PATH>
Path to JSON/YAML file containing additional risks.
--custom-risk-list-json <JSON>
JSON string containing additional risks.
--custom-false-positive-considerations <LIST>
Additional considerations to reduce false positives.
GitHub Actions Integration
- Easy Setup
- GitHub App
- Block Pull Request
Simple setup with no GitHub token requiredWhat this does:
- ✅ Adds risk assessment comments to pull requests
- ❌ No team notifications or reviewer requests
- ❌ No status checks or PR blocking
Available workflow_args
| Argument | Type | Default | Description |
|---|---|---|---|
approver | string | "" | GitHub username or group to notify for approval |
should-block-pull-request | boolean | false | Whether to block the pull request until security review is complete |
custom-risk-list-action | string | "append" | Whether to "append" to or "replace" the default risks list |
custom-risk-list-filepath | string | null | Path to JSON/YAML file containing additional risks |
custom-risk-list-json | object | null | JSON object containing additional risks to consider |
custom-false-positive-considerations | array of strings | [] | List of additional considerations to help reduce false positives |
slack-webhook-url | string | null | Provide a Slack webhook URL to send notifications |
no-gh-comment | boolean | false | Set to true to disable GitHub comments for risk findings |
confidence | integer (1-10) | 7 | Minimum confidence threshold for filtering findings |
chunk-size | integer | 500 | Number of lines per chunk |
limit | integer | null | Limit the number of files to scan |
globs | array of strings | null | File patterns to include (uses workflow defaults if not provided) |
max-concurrent-chunks | integer | 5 | Maximum number of chunks to process concurrently |
github-app-id | string | No | GitHub App ID for enhanced GitHub integration (enables team notifications and PR blocking) |
github-app-private-key | string | No | GitHub App private key for enhanced GitHub integration (enables team notifications and PR blocking) |
